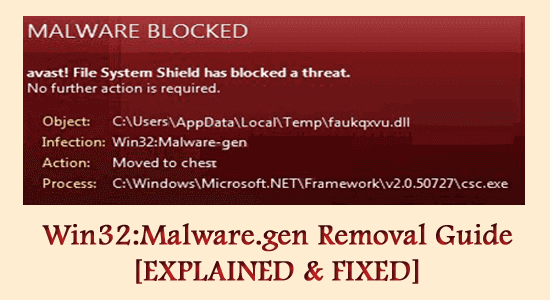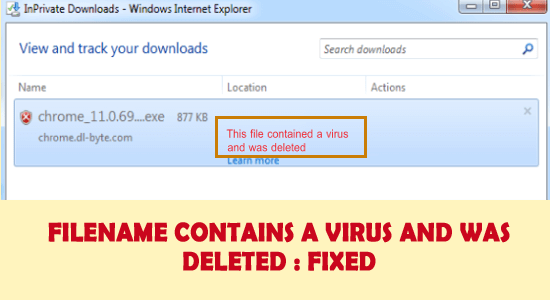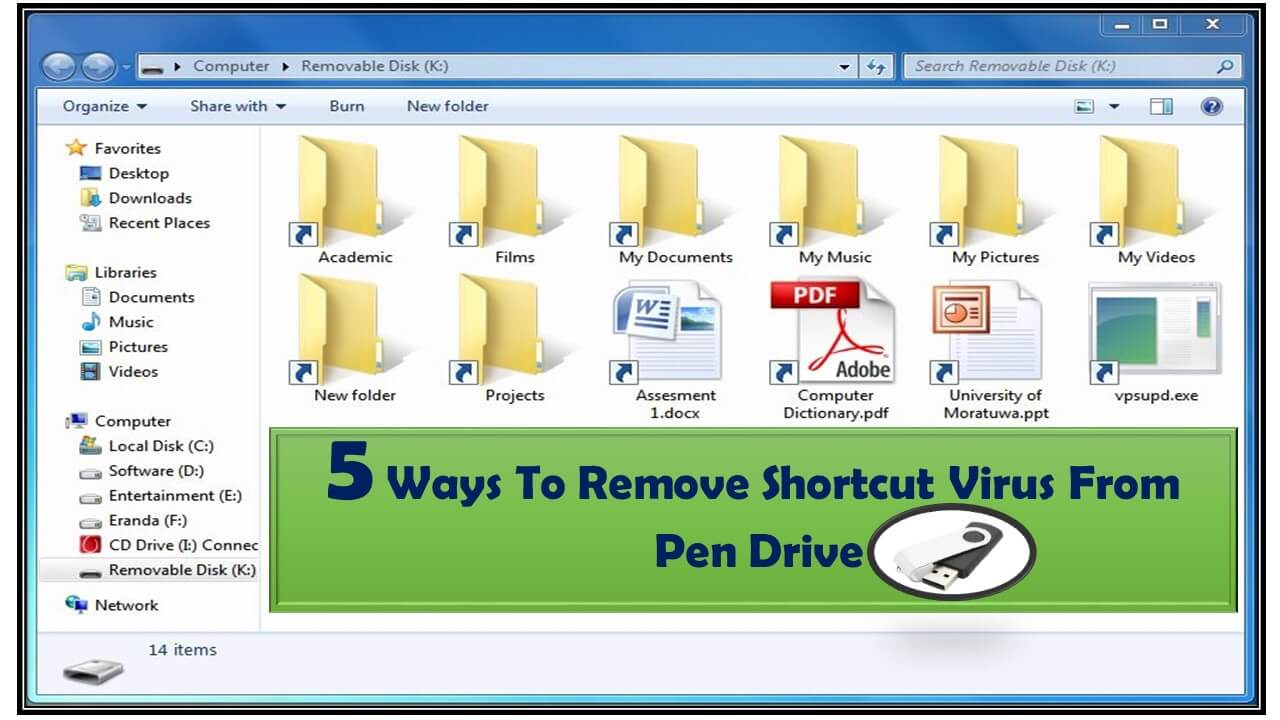
Antivirus and anti-malware are two types of security software designed to protect your devices from different types of threats. While their functions overlap to some extent, there are some notable differences between them.
Hardeep has always been a Windows lover ever since she got her hands on her first Windows XP PC. She has always been enthusiastic about technological stuff, especially Artificial Intelligence (AI) computing. Before joining PC Error Fix, she worked as a freelancer and worked on numerous technical projects.