In the world of IT Ransomware is a much-debated topic. As Ransomware is continuously evolving thus it’s become tough to keep track of several strains of Ransomware. But it is seen that each variety of Ransomware shows some unique style of spreading.
Get complete knowledge of the different type of Ransomware variants. So, that you can easily identify and smartly deal with it.
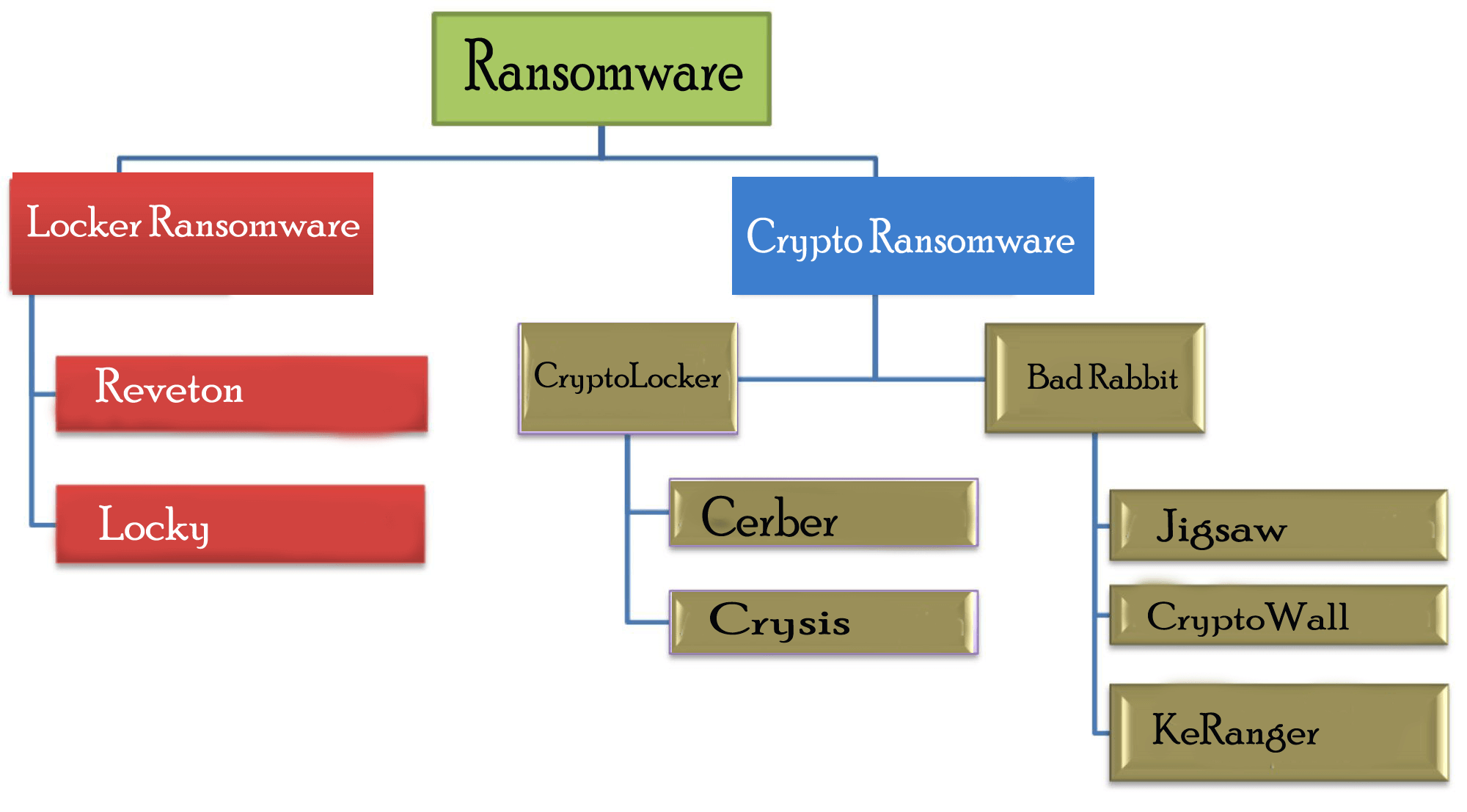
Types Of Ransomware
Mainly Ransomware is divided into two categories:
1: Locker Ransomware: Locker Ransomware locks victims’ devices so as to prevent them from using it. After locking out, cybercriminals demands for ransom money to decrypt the device.
2: Crypto Ransomware: Crypto Ransomware prevents users to access their files or data, by encrypting it. After then Cybercriminals demands for the money to retrieve their files back.
Now that you have understood what are the main categories of Ransomware exists. It’s time to explore your knowledge of different types of Ransomware that comes under each of these Ransomware categories.
Let’s know how different and hazardous each type of Ransomware can be.
Hierarchical Representation Of Ransomware Types And Variants
Let’s catch complete detail on each Ransomware type….!
Locker Ransomware

1. Reveton Ransomware:
| Name | Reveton |
| Threat Type | Locker Ransomware |
| Symptoms | This Ransomware type locks the user’s device by preventing them to get a login. After then it shows a fake official-appearing message claimed by National Police Force or from the FBI. |
| Distribution methods | Through Torrent websites, malicious ads. |
| Damage | The whole PC is encrypted and without paying ransom money you can’t open it. Additionally, malware infection and password-stealing Trojans can be installed along with the Ransomware infection. |
Screenshot Of Reveton Ransomware:
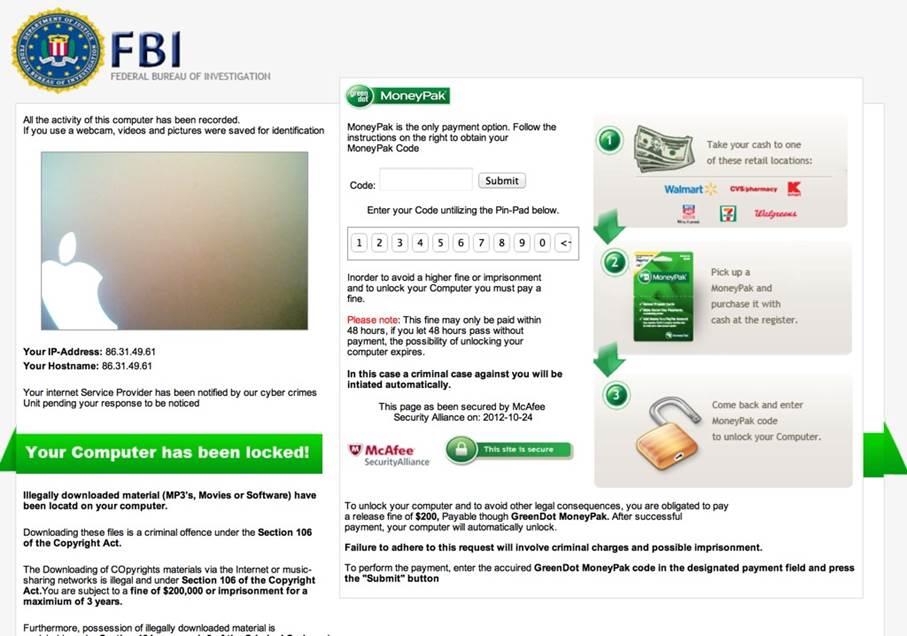
Reveton Ransomware came into existence at the end of 2012. This Ransomware type locks the user’s device by preventing them to get a login. After then it shows a fake official-appearing message claimed by National Police Force or from the FBI.
This fake official message includes a declaration regarding the involvement of the user in illegal activities such as software piracy or child pornography. After encountering this type of Ransomware victim has no more control over their device.
2. Locky Ransomware:
| Name | Locky |
| Threat Type | Locker Ransomware |
| Symptoms | PC’s infected with the Locky Ransomware will show a ransom demand note either in the form of text file or like a desktop wallpaper.
Locky Ransomware Encrypted files includes the following extension: .loptr, .asasin, .diablo6, .aesir, .locky,.odin, .zepto, .osiris, .shit, .thor, .ykcol, |
| Distribution methods | This Ransomware species spreads through exploit kits (EKs) & malspam. In the past Neutrino, RIG, and Nuclear EKs have distributed this Locky Ransomware |
| Damage | Systems attacked by Locky Ransomware become unusable because all the files that are mainly required for regular operation are got encrypted. |
Screenshot Of Locky Ransomware:
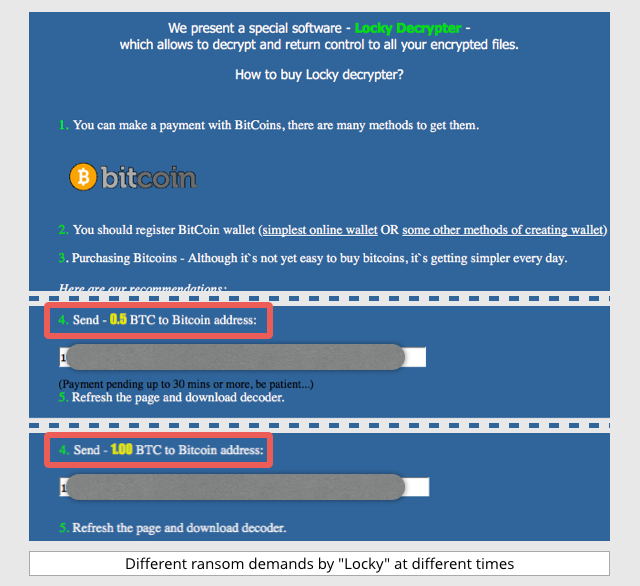
Locky is another very nasty type of Ransomware that is first rolled out in the year 2016 attack by a well-organized hacker’s group. This variant of Ransomware is mainly designed for locking up the victim’s device and prevent it’s accessing until the ransom is completely been paid.
This Ransomware type has the ability to encrypt around 160 different file types which are mostly used by testers, engineers, designers, and developers, etc.
It attacks the victim’s device by tricking them to install this creepy Ransomware through fake emails along having malicious attachments. Well, this technique of malware transmission is popularly called as “phishing”.
This malware makes uses of a kind email message that camouflaged as an invoice. When users open such email attachments automatically the invoice gets disappear. After then users are asked to enable the macros for reading out the document. Once the user enables macros, Locky Ransomware starts encrypting multiple file types by making use of the AES encryption.
Apart from the list of ransomware mentioned above, Petya, NotPetya, TeslaCrypt, TorrentLocker, ZCryptor, etc., are some of the other ransomware variants that are well-known for their malicious activities.
Crypto Ransomware
1.CryptoLocker Ransomware
|
Name |
CryptoLocker |
| Threat Type | Crypto Ransomware |
| Symptoms | You are completely unable to open any of your system stored files. Functional files extension appears changed to you eg: my.docx.locked.
On your desktop, a ransom payment message appears. Cybercriminals ask for payment of ransom money in “Bitcoins” for unlocking up your encrypted files. |
| Distribution methods | CryptoLocker usually spread through fake emails claims to come from legitimate businesses by UPS tracking notices and phony FedEx. |
| Damage |
The Ransomware has the capability to search and encrypt files saved within the external hard drives, shared network drives, network file shares, USB drives, or data present on the cloud storage drives. |
Screenshot Of CryptoLocker Ransomware:
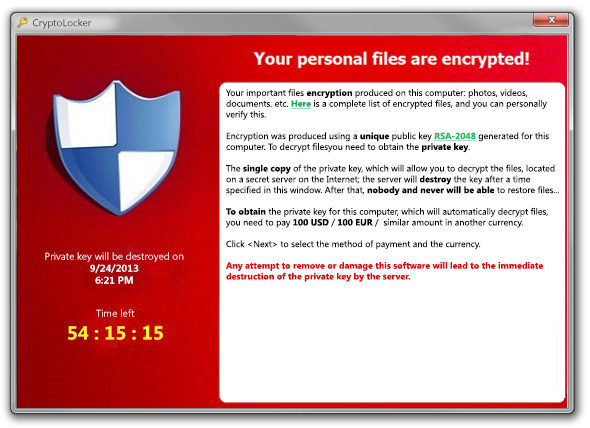
CyptoLocker Ransomware is released in the year 2013 when the hackers had used the CryptoLocker botnet (oldest form of cyber attack) approach in the Ransomware.
It is one of the most destructive types of Ransomware as it uses powerful encryption algorithms. So, it’s almost impossible to get back the Crypto Ransomware-infected device and documents without submitting the ransom money.
This Ransomware follows a non-familiar path of encrypting users’ data. For each file, CyptoLocker Ransomware randomly creates a symmetric key. After then this symmetric key is been encrypted using a public asymmetric key. At last, it is added to the file.
After successfully encrypting the files, Ransomware throws a ransom demand message to the user. So, the victim has to pay the money if they want the private asymmetric key for decrypting the symmetric keys applied to each encrypted file.
If payment of done before the deadline then the hacker will delete the symmetric key. After which the data recovery is next to impossible.
2. Bad Rabbit Ransomware
|
Name |
Bad rabbit |
| Threat Type | Crypto Ransomware |
| Symptoms | This is bootkit-based ransomware like Petya and NotPetya. Usually, it is seen that a file with the name “install_flash_player.exe” is inserted on the host through the website users have to execute this manually.
Once you execute this, it starts encrypting the files present on the target device. Very soon it installs its own boot loader in the MBR also sets a schedule for a system reboot. After rebooting the system, it will show the ransom note on users’ display. |
| Distribution methods | This Ransomware species spread through Adobe Flash updates, by giving a false warning regarding Flash player update. It’s a trick to trap users to make a click on the suspicious link for the update. |
| Damage |
Bad Rabbit is well capable to proliferate through SMB. This Ransomware looks for open shares and executes the Mimikatz software for obtaining the Windows credentials. After then the virus makes uses of the list of hard-coded logins and passwords to damage other PC over the network through SMB. |
Screenshot Of Bad Rabbit Ransomware:
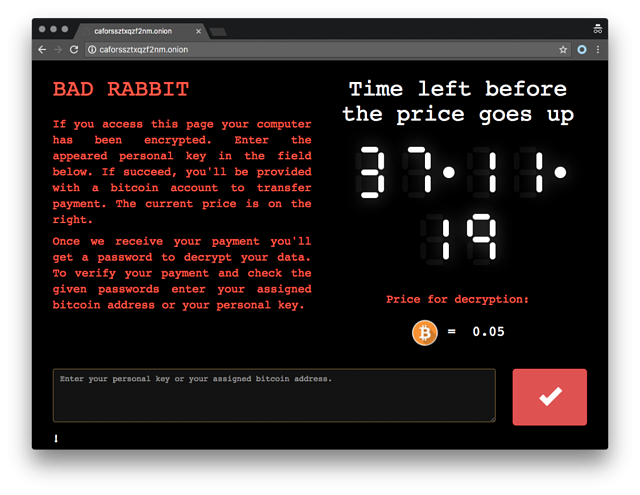 Bad Rabbit is one such type of Ransomware that has severely infected organizations across Eastern Europe and Russia. This Ransomware species make use of fake Adobe Flash update over the compromised websites for its distribution.
Bad Rabbit is one such type of Ransomware that has severely infected organizations across Eastern Europe and Russia. This Ransomware species make use of fake Adobe Flash update over the compromised websites for its distribution.
3. Cerber Ransomware
| Name |
Cerber |
| Threat Type |
Crypto Ransomware |
| Symptoms | After the intervention of this Ransomware through the email along with a JavaScript attachment, it starts executing. The script gets connected with the internet and starts downloading the payload which actually responsible for the encryption process.
Downloaded Payload attacks the system files and transforms the desktop wallpaper into a ransom demand note. You will get this ransom note in almost every folder infected with this Ransomware species. |
| Distribution methods | Hacker offers Cerber Ransomware to the victim in two ways:
1. Through the malicious email having a double zipped file with a Windows Script File. 2. At the bottom of the phishing email, there is an unsubscribe link. This new technique of damaging is done by the Rig and Magnitude exploit kits. Both of these exploit kits are using 0-day vulnerabilities. |
| Damage |
The affected system gets unusable because all the files mainly used for regular operations are got encrypted. Hackers don’t return the data held hostage back to the victim even after the ransom has been paid. Cybercriminals either sell it on the black market or make a duplicate user’s profile to perform fraud activity. |
Screenshot Of Cerber Ransomware:
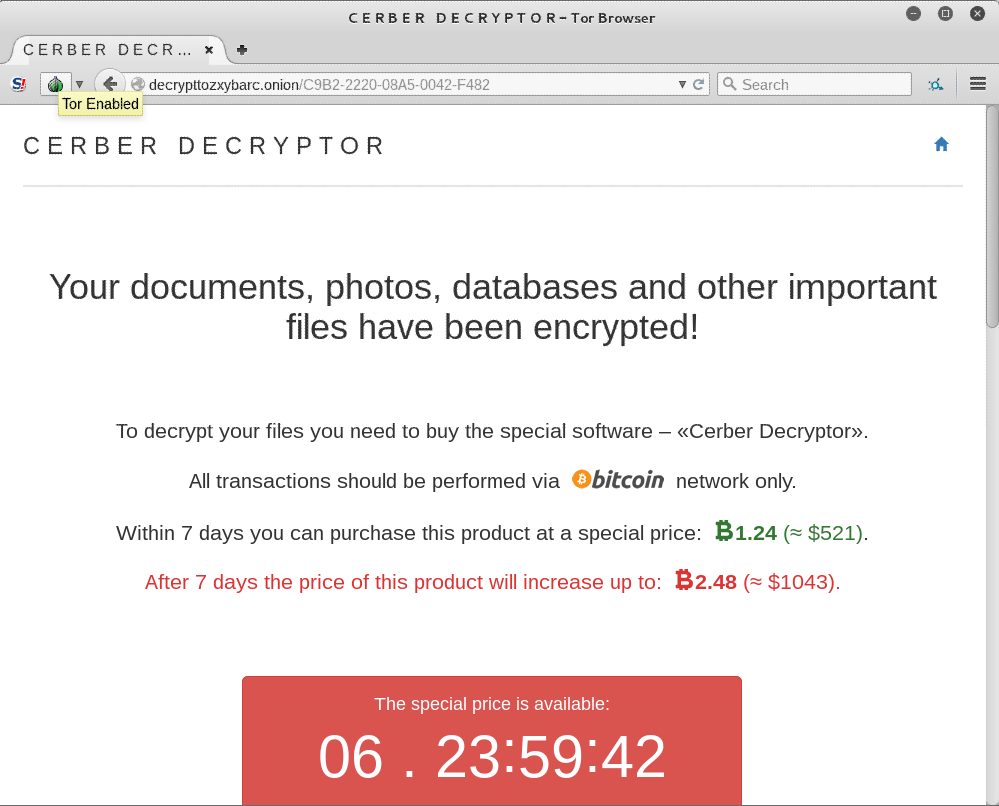
Another Ransomware type is Cerber which mainly aims the cloud-based Office 365 audience. Several million Office 365 customers have already caught into the phishing campaign executed by the Cerber Ransomware.
4. Crysis Ransomware
| Name | Crysis |
| Threat Type | Crypto Ransomware |
| Symptoms |
After getting into the PC, CrySiS Ransomware starts file encryption and very soon all your documents, images, database, music videos, and other stuff gets encrypted. Initially, you will notice all your encrypted file seems to append with a .CrySis extension. Later on, different extensions is been used. After then a ransom note like README.txt, Decryption instructions.txt, Infohta, etc. is also dropped just to inform victims about what happened to their system files. This ransom note contains the detail about the decrypting files and ransom payment. |
| Distribution methods | This Malware species make use of malicious phishing emails, weakly protected RDP connections, and sometimes offers a download for installing the game or legitimate software. |
| Damage | Ransom.Crysis starts deleting the restore point by executing the vssadmin delete shadows /all /quiet command.
If your backup plan contains these restore points then execution of this Ransomware very soon starts deleting it off. |
| Encryption algorithm | Crysis ransomware uses a combination of RSA, AES. Whereas as in some cases DES ciphers is used for locking up the personal data. |
| Ransom note | Hackers initially give ransom note in the form of README.txt; later two more ransom demand note dropped on the system like FILES ENCRYPTED.txt and Info.hta |
Screenshot Of Crysis Ransomware:
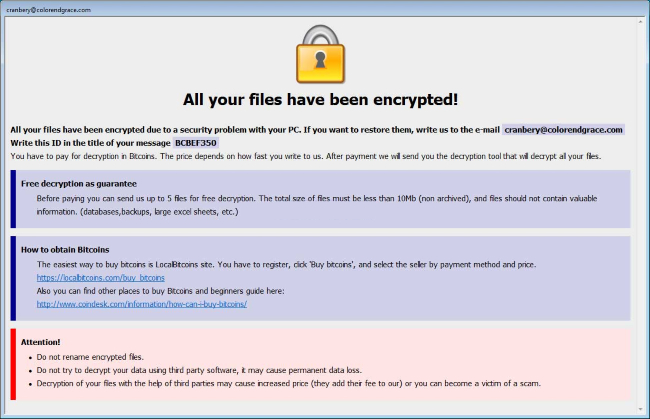
Another very unique type of Ransomware variant is Crysis. This Ransomware only encrypts files present on some fixed drive space, removable drives, or in the network drives.
This Ransomware species make use of malicious email attachments with dual file extensions for distribution. It’s just impossible to decrypt the encrypted file by Crysis Ransomware because it uses a strong encryption algorithm.
5. Jigsaw Ransomware
| Name | Jigsaw |
| Threat Type | Crypto Ransomware |
|
Symptoms |
You will see after the intervention of the Jigsaw Ransomware all your personal file gets encrypted with .pleaseCallQQ, .jes, .booknish, .paytounlock, .fun, .choda, .black007, .tedcrypt , .pay, .dat, .hacked.by.Snaiparul, .FUCKMEDADDY, .lockedgood, .venom like extensions.
Very soon your desktop wallpaper is changed to ransom note and serve you with problems like system slowdowns, High CPU consumption. |
| Distribution methods | Generally, jigsaw Ransomware spreads through the mean of malicious spam emails. This virus encrypts the data by making use of the AES cipher and attaches one of the above-mentioned extensions. Furthermore, this will drop a ransom note along with the image of a very popular character “Saw”. The ransom note contains a complete explanation of the current situation and the ransom amount. |
| Damage |
Jigsaw Ransomware encrypts around 226 different file types attached with the extension .FUN, .BTC, and .KKK extensions using the AES encryption algorithm. You will see that on the ransom note there is a 60-minute timer that counts down to zero. After reaching 0 hackers will delete certain files. |
Screenshot Of Jigsaw Ransomware:
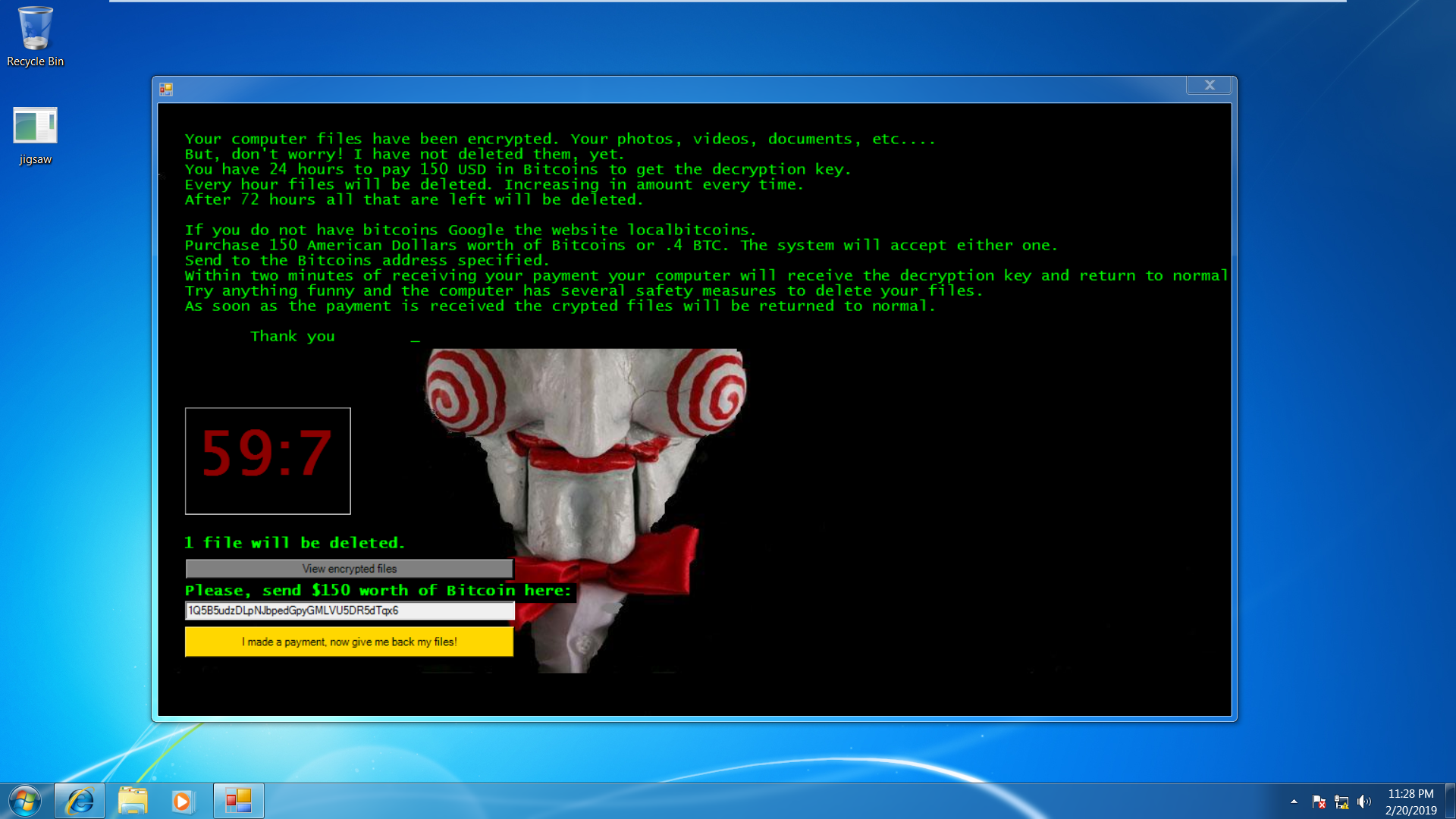
In the list of the most destructive type of Ransomware variants “Jigsaw Ransomware” is the first one. This Ransomware encrypts the victim’s data file and rapidly starts deleting it if the ransom is not cleared soon. The deletion of files gradually starts one by one in the gaping of 1 hour if the ransom amount was not paid.
6. CryptoWall Ransomware
| Name |
CryptoWall |
| Threat Type | Crypto Ransomware |
| Symptoms |
At first, you will receive a spam email from the cyber-criminals having the forged header information, which makes you believe that it comes from a shipping company like DHL or FedEx. This spam email contains a message regarding the failure of package delivery or shipment of the item you have ordered. It’s almost impossible to avoid these emails to get opened. Once you click to open it your system is infected with the CryptoWall virus. |
| Distribution methods | CryptoWall is distributed through various means like drive-by downloads browser, exploit kits and attachment of malicious mail. |
| Damage |
CryptoWall Ransomware makes use of strong public-key cryptography for distorting files by appending specific extensions into it. |
Screenshot Of CryptoWall Ransomware:
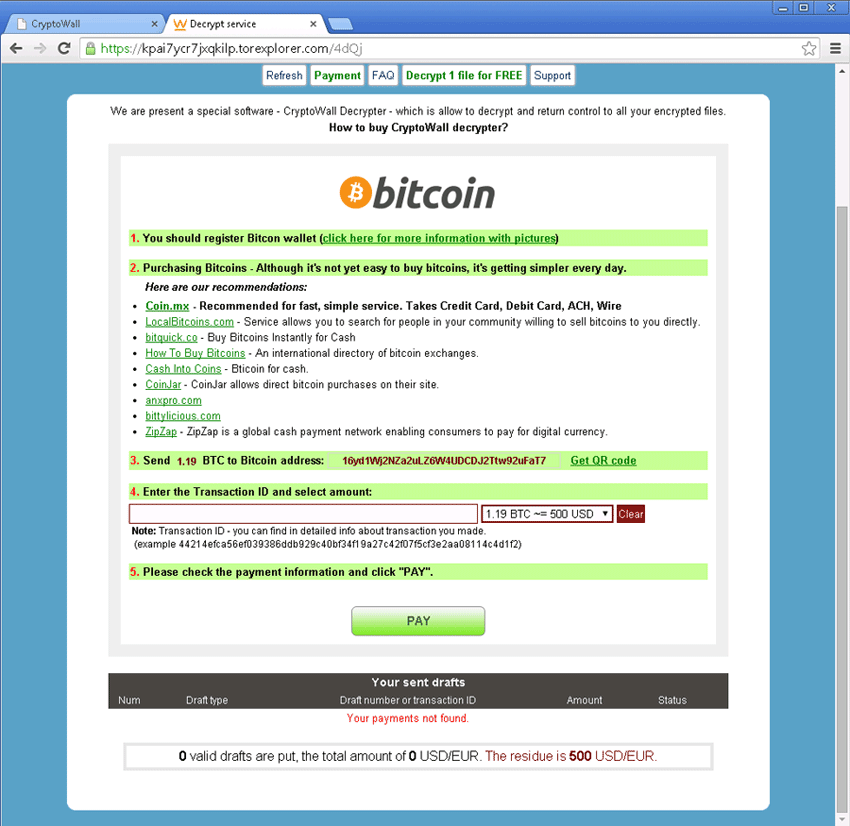
Firstly the CryptoWall Ransomware variant appeared in the year 2014. After then it appeared in various names and versions like CryptorBit, CryptoWall 2.0, CryptoWall 3.0, CryptoDefense and CryptoWall 4.0.
One very catchy feature of this Ransomware is that the hacker offers a one-time usable decryption service only for one file. This is just to make-believe to their victim that they have actually kept the decryption key.
This Ransomware uses so many tricks to get distribute itself some common one includes:
- Malicious attachments in emails claiming its approval from the financial institutions.
- The intervention of exploit kits which exploit vulnerabilities in the software of victim
- Through malicious web pages and ransom displaying of malicious ads.
- some types of CryptoWall Ransomware also give you a fake note declaration like:
“Congratulations!!! You have become a part of a large community CryptoWall. Together we make the Internet a better and safer place.”
7. KeRanger Ransomware
| Name |
KeRanger |
| Threat Type | Crypto Ransomware |
| Symptoms |
When any user installs and executes the transmission application’s malicious version then automatically an included file named General.rtf gets copied to ~/Library/kernel_service location and starts executing. After copying of this file on the location kernel_service it’s execution starts and it will create two files known as ~/Library/.kernel_pid and ~/Library/.kernel_time. The file kernel_pid is having the process ID for the execution of the kernel_service process. On the other hand file name .kernel_time includes the timestamp about the first time execution of the Ransomware execution. |
| Distribution methods | This Ransomware comes included within a Trojanized version of one very popular BitTorrent installer Transmission. To make victims foolish as it appears properly signed by the genuine Apple developer certificate. |
| Damage | KeRanger Ransomware is designed in such a way that it starts encrypting the files present on the infected PC after passing of 3 days of the original infection. |
Screenshot Of KeRanger Ransomware:
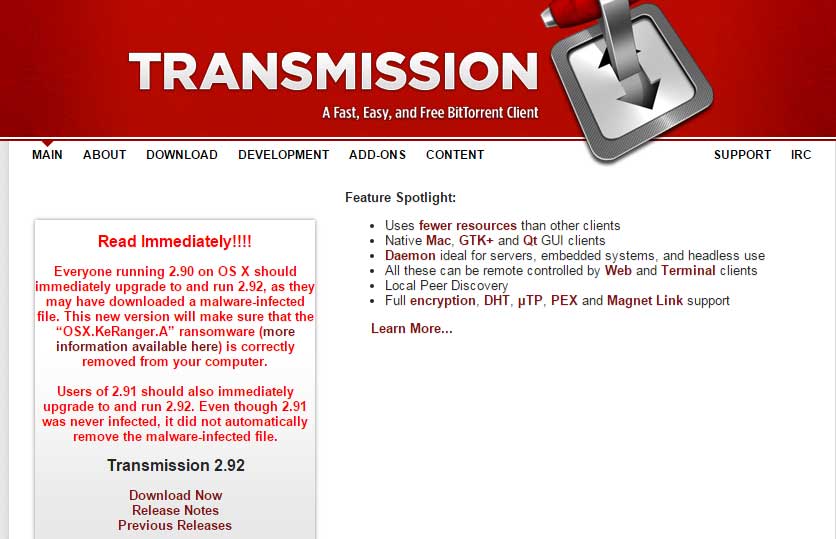
KeRanger Ransomware variant was rolled out in the year 2016. It is found that it is the first type of Ransomware that has successfully infected a Mac OS X PC. This Ransomware is injected within the installer of the open-source bit torrent client. The user who downloads such an infected installer easily caught into the trap made by KeRanger Ransomware.
After infecting your device, this Ransomware waits for only 3 days after that it encrypts around 300 file types. In the next steps, it starts sending you a text file in which there is a demand for Bitcoin along with the method to pay seems mentioned.
Conclusion:
Even though, Ransomware is counted as a most hazardous threat for the device and your data. But by following a habit of safe computing and using updated security software, it’s become too easy to stay protected from any kind of Ransomware. You just make your portion of the task i.e always being attentive while surfing and install trusted security software.
Unfortunately, if your system is already hijacked with malware species then try Malware Removal Tool for easy removal of virus from your PC.
Hardeep has always been a Windows lover ever since she got her hands on her first Windows XP PC. She has always been enthusiastic about technological stuff, especially Artificial Intelligence (AI) computing. Before joining PC Error Fix, she worked as a freelancer and worked on numerous technical projects.