Cybercriminals are constantly devising several innovating tricks and tactics to spread Adware. Having ideas of what trending Adware spreading techniques are followed by cyber-crooks is very important to prevent your device from the risk of Adware attacks.
So, catch complete detail on different means through which Adware gets into your PC.
Adware Spreading Techniques Followed By Cyber-Crooks
1. Email Phishing:

Propagating Adware like malicious programs by email is quite an effective and simple trick to perform. Cybercriminals send Adware programs that start collecting the data from the moment such malicious email attachments get opened.
These emails make you believe that it comes from some trusted sources. Like the U.S. Postal Service, user’s bank, FedEx or from any trusted contacts within the user’s own list.
It is also seen that some suspicious emails also infect your PC from email client’s preview pane even if you don’t open or download any link or attachments.
Most of these malicious emails also contain such links that take the user towards the fake version of their bank’s website. After then force them to change their password. Once the user does this, Adware will collect the entire credential user’s login detail and then send it to the cybercriminal.
2. Internet Surfing:

Today Web browsing is an essential need for any net surfer but it also exposes your PC to numerous risks. Cybercriminals design websites that exploit system vulnerabilities. After visiting such a website your system starts showing fake pop-up ads and warnings regarding virus attack on your PC.
Once you click on the OK option to clean the system registry the Adware malware gets an easy chance to install on your host system. Some Adware variants are also responsible for DNS redirects or browser exploitation.
3. Outdated Software:

Adware malware crawls over the internet to look for the vulnerabilities of outdated software. So as to, acquire an easy chance to get in your PC.
Every web surfer needs to care if they are browsing the web with outdated software. Whether, they are using an outdated browser, operating systems or plug-ins, etc.
4. Local Area Networks (LANs):
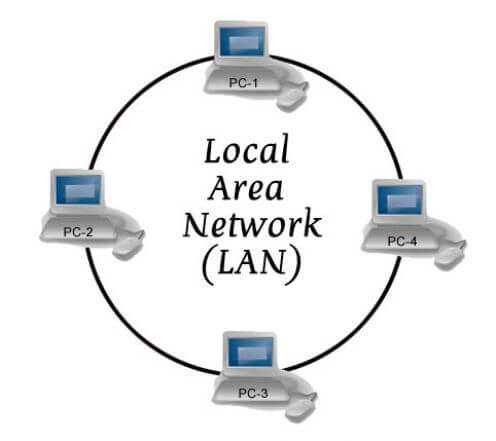
We all know LAN is a collection of locally connected PC which share information over the private network. If one of your PC gets infected with Adware species, then the entire connected PC on the same LAN network will also catch the same infection.
5. File Transfer & Network Sharing:

File transfer using FTP can invite Adware and associated threats attack using Networks.
Network sharing is a common thing that is required by any Internet user and by considering that cyber crooks develop the latest ideas to insert infection using networks.
6. Social Networks:

Cybercriminals mostly prefer the crowds. With the vast growth in social networks, cyber crooks at first approach to exploit system security.
To accomplish this task, hackers create fake celebrity profiles which are when clicked on, will deploy the malware onto their device. After then the hacker will dig the infected PC for credential login details of users on financial websites.
It is also found that Adware attackers scan the LinkedIn profile to catch the user’s details and get their contact number. After then make a call pretending to be from the IT department and ask for bank login details.
7. Pop-ups:
Some Adware gets in your PC through camouflaged screen pop-up ads which shows genuine alerts or warnings.
One very tricky and well-known Adware “hoax pop-up” claims for scanning your PC and detecting the Adware species on your PC. Once you caught in its trap and click for removing the Adware program with its provided tool. In this way, you are actually inviting the Adware to get into your PC.
8. Removable Computer storage media:

Adware malware spreads through sharing the computer storage media with DVDs, CDs, USB sticks and USB drives. These are some common ways through which adware propagates and attacks on your PC.
When any user transfers files/documents from an infected system to a healthy PC with any of these removable storage media. Then automatically the infection will enter into your healthy PC as well.
Always make a habit of scanning the storage media devices before copying or open the data. This will ultimately reduce the possibilities of data corruption and security risks.
9. Injection Of Infected Codes:

Another very sneaky way through which Adware gets in your PC is by running an infected code as JavaScript within a web browser. Adware also exploits security holes for infecting locally installed programs with an injection of malicious codes.
Some of the Email clients execute JavaScript and HTML codes embedded in Email messages.
Whereas, most of the webmail services and email clients are having, such built-in security features that easily overcome this issue on its own.
10. Drive-By Downloads From Suspicious Website:

Most common means through which Adware spreads are using bundled software, browser/toolbar extensions, and downloads offered by pop-ups.
Adware serves you with common kinds of stuff that most of the users commonly search for like a video player or plug-in. Adware comes hidden within legitimate software or plug-ins. Apart from this Adware distributed through downloaded files from torrent and software sites.
Now a day’s Adware is also taking its steps toward Google Play Store and infilling the Android devices with many of its garbage data.
A very common method trending nowadays used for delivering Adware malware is deception. Malware makers trick users in such a way that users themselves allow installation of unwanted programs along with downloading programs. To accomplish these Adware makers usually perform the following changes:
- In the installation criteria sudden occurrence of pre-populating checkboxes
- The option of skip either grey out or minimized to such extent that it won’t appear.
- Inserting the recommended option next to the preferred option.
To avoid Adware intrusions on your device just read the install wizards instruction and EULAs((end-user license agreement) with the hawk-eyed accuracy.
Wrap Up:
After reading the above post on “How Adware Spreads”, you all must have got a clear idea on how Adware gets into your PC during regular Web surfing. If you won’t remove it instantly then this malicious Adware program may transmit all your credential information to cyber-crooks.
Adware not only poses privacy and security threats, but it also slows down your system performance. Well, the reason behind your system performance drop-down is the overconsumption of resources required to process and transmit data. Sometimes the computer fails to process legitimate programs because of the toll it brings to your computer.
Apart from computer crashing, slow system performance, these types of programs may leave security holes that make your computer susceptible to exploitation by hackers. These kinds of threats are very dangerous for your PC. So, remove Adware threats as soon as possible with the help of some reliable Malware removal tool.
Your attentiveness is the first step to prevent Adware attacks. So, Always Be Attentive….!
Hardeep has always been a Windows lover ever since she got her hands on her first Windows XP PC. She has always been enthusiastic about technological stuff, especially Artificial Intelligence (AI) computing. Before joining PC Error Fix, she worked as a freelancer and worked on numerous technical projects.